This is the write up for the room Mitre on Tryhackme and it is part of the Tryhackme Cyber Defense Path
Make connection with VPN or use the attackbox on Tryhackme site to connect to the Tryhackme lab environment
Tasks Mitre on tryhackme
Task 1
Read all that is in the task and press complete
Task 2
Read all that is in the task and press complete
Task 3
Open Phishing, Technique T1566 – Enterprise | MITRE ATT&CK®
3.1 Only blue teamers will use the ATT&CK Matrix? (Yay/Nay)
Answer: Nay
3.2 What is the ID for this technique?
We can find this on the page right corner
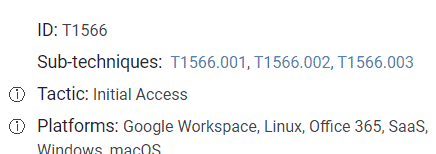
Answer: T1566
3.3 Based on this technique, what mitigation covers identifying social engineering techniques?

Answer: User Training
3.4 There are other possible areas for detection for this technique, which occurs after what other technique?

Answer: User Execution
3.5 What group has used spear phishing in their campaigns?

Answer: Dragonfly
3.6 Based on the information for this group, what are their associated groups?
Click on the link Dragonfly Dragonfly, TG-4192, Crouching Yeti, IRON LIBERTY, Energetic Bear, Group G0035 | MITRE ATT&CK®

Answer: TG-4192,Crouching Yeti,IRON LIBERTY,Energetic Bear
3.7 What tool is attributed to this group to transfer tools or files from one host to another within a compromised environment?

Answer: PSexec
3.8 Based on the information about this tool, what group used a customized version of it?
Click on the link PSexec PsExec, Software S0029 | MITRE ATT&CK®

3.9 This group has been active since what year?
Click on the link FIN5 FIN5, Group G0053 | MITRE ATT&CK®
Answer: 2008
3.10 Instead of Mimikatz, what OS Credential Dumping tool is does this group use?

Answer: Correct Answer
Task 4
4.1 For the above analytic, what is the pseudocode a representation of?

Answer: Splunk Search
4.2 What tactic has an ID of TA0003?
Go to mitre.org and type in the searchbox TA0003. Once found I notice the URL
Persistence, Tactic TA0003 – Enterprise | MITRE ATT&CK®
Answer: Persistence
4.3 What is the name of the library that is a collection of Zeek (BRO) scripts?
Head to https://car.mitre.org/ and search for Zeek

Answer: BZAR
4.4 What is the name of the technique for running executables with the same hash and different names?

Answer: Masquerading
4.5 Examine CAR-2013-05-004, what additional information is provided to analysts to ensure coverage for this technique?
Go to this URL CAR-2013-05-004: Execution with AT | MITRE Cyber Analytics Repository

Answer: Unit Tests
Task 5 – Shield ( This has been replaced by Mitre Engage, Questions are still the same )
Open Shield Home (mitre.org) ( Deprecated ) You now have a machine attached to this task
Start the machine attached to this task
5.1 Which Shield tactic has the most techniques?
Head over to Active Defense Matrix (mitre.org). We can see Detect has the most
Answer: Detect
5.2 Is the technique ‘Decoy Credentials’ listed under the tactic from question #1? (Yay/Nay)

Answer: Yay
5.3 Explore DTE0011, what is the ID for the use case where a defender can plant artifacts on a system to make it look like a virtual machine to the adversary?
Go to the techniques Active Defense Techniques (mitre.org)
Then Click on DTE0011 and notice it is a Decoy Content. Scroll further down

Answer: DUC0234
5.4 Based on the above use case, what is its ATT&CK® Technique mapping?
Navigate to https://shield.mitre.org/attack_mapping/mapping_all.html
Answer: T1497
5.5 Continuing from the previous question, look at the information for this ATT&CK® Technique, what 2 programs are listed that adversary’s will check for?
Answer: Sysinternals and Wireshark
Task 6
6.1 How many phases does APT3 Emulation Plan consists of?

Answer: 3
6.2 Under Persistence, what binary was replaced with cmd.exe?
The answer can be found in the PDF https://attack.mitre.org/docs/APT3_Adversary_Emulation_Plan.pdf

Answer: sethc.exe
6.3 Examining APT29, what 2 tools were used to execute the first scenario?
The answer can be found in scenario1 infrastructure adversary_emulation_library/Infrastructure.md at master · center-for-threat-informed-defense/adversary_emulation_library · GitHub
Answer Pupy and Metasploit
6.4 What tool was used to execute the second scenario?
The answer can be found in scenario 2 infrastucture
Answer PoshC2
6.5 Where can you find step-by-step instructions to execute both scenarios?
Answer: ATT&CK Arsenal
Task 7
7.1 What is a group that targets your sector who has been in operation since at least 2013?
Answer: APT33
7.2 Does this group use Stuxnet? (Yay/Nay)
APT33, HOLMIUM, Elfin, Group G0064 | MITRE ATT&CK®
Answer: Nay
7.3 As your organization is migrating to the cloud, is there anything attributed to this APT group that you should focus on? If so, what is it?

Answer: Cloud Accounts
7.4 What tool is associated with this technique?
Valid Accounts: Cloud Accounts, Sub-technique T1078.004 – Enterprise | MITRE ATT&CK®
Answer Ruler
7.5 Per the detection tip, what should you be detecting?

Answer abnormal or malicious behavior
7.6 What platforms does this affect?

Answer Azure AD, Google Workspace, IaaS, Office 365, SaaS
And this concludes the Mitre on Tryhackme
Great designs and products for your hacker’s cave
You can get these designs on more than 70 products ranging from
- T-shirt
- mugs
- mousepad
- baseball caps
- Metal prints
- Art Board
And much more.











