This is the write up for the room Nessus on Tryhackme and it is part of the CompTIA Pentest+ Path
Make connection with VPN or use the attackbox on Tryhackme site to connect to the Tryhackme lab environment
Tasks Nessus
Task 1
This task will let you install Nessus on an Kali VM. Just follow the guide in the task and you’ll be fine
Task 2
2.1 What is the name of the button which is used to launch a scan?
Answer: New Scan
2.2 What side menu option allows us to create custom templates?
Answer: Policies
2.3 What menu allows us to change plugin properties such as hiding them or changing their severity?
Answer: Plugin Rules
2.4 In the ‘Scan Templates’ section after clicking on ‘New Scan’, what scan allows us to see simply what hosts are alive?
Click on new scan

Answer: Host Discovery
2.5 One of the most useful scan types, which is considered to be ‘suitable for any host’?

Answer: Basic Network Scan
2.6 What scan allows you to ‘Authenticate to hosts and enumerate missing updates’?
Answer: Credentialed Patch Audit
2.7 What scan is specifically used for scanning Web Applications?

Answer: Web Application Tests
Task 4
Boot up the machine attached to this task
4.1 Create a new ‘Basic Network Scan’ targeting the deployed VM. What option can we set under ‘BASIC’ (on the left) to set a time for this scan to run? This can be very useful when network congestion is an issue.
Click on new scan then on Basic Network Scan
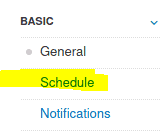
Answer: Schedule
4.2 Under ‘DISCOVERY’ (on the left) set the ‘Scan Type’ to cover ports 1-65535. What is this type called?
Click on dicovery then under the scan type select Port scan (all ports)
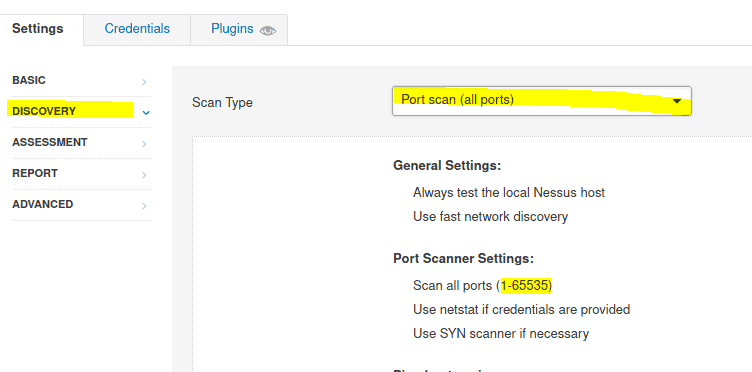
Answer: Port scan (all ports)
4.3 What ‘Scan Type’ can we change to under ‘ADVANCED’ for lower bandwidth connection
Click on advanced en under scan type we see Scan low bandwidth links
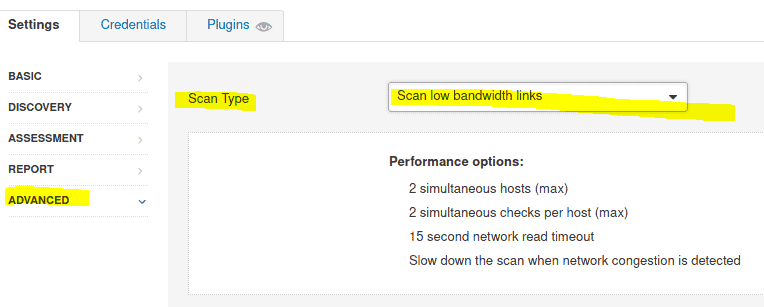
Answer: scan low bandwidth links
4.4 After the scan completes, which ‘Vulnerability’ in the ‘Port scanners’ family can we view the details of to see the open ports on this host?
We still nee to confiure the target. Go to general
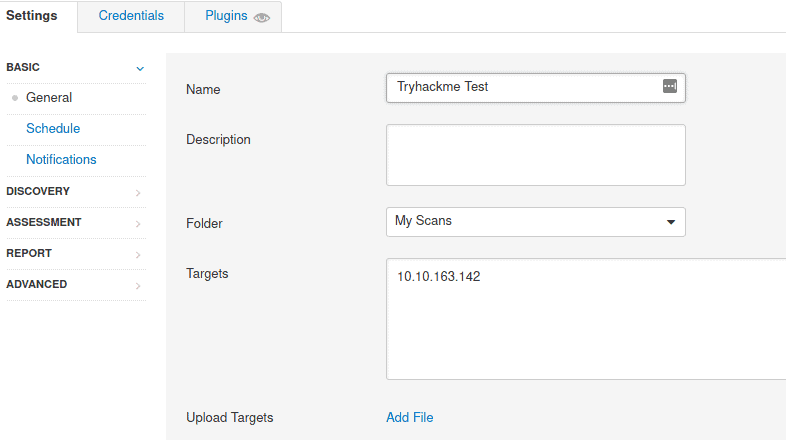
At targets fill in the IP of the machine
Then launch the scan. It will take a while
When scan is complete. Click on All Scans and click the scan we just created
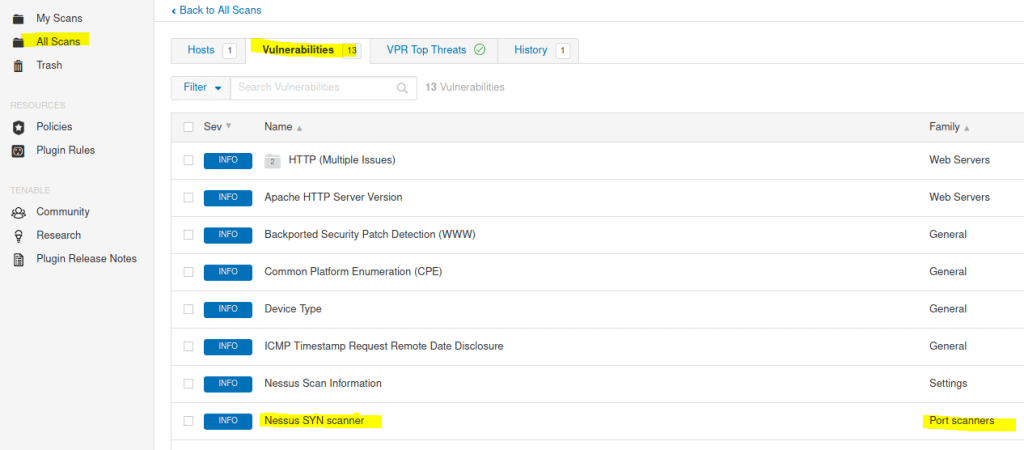
Answer: Nessus SYN Scanner
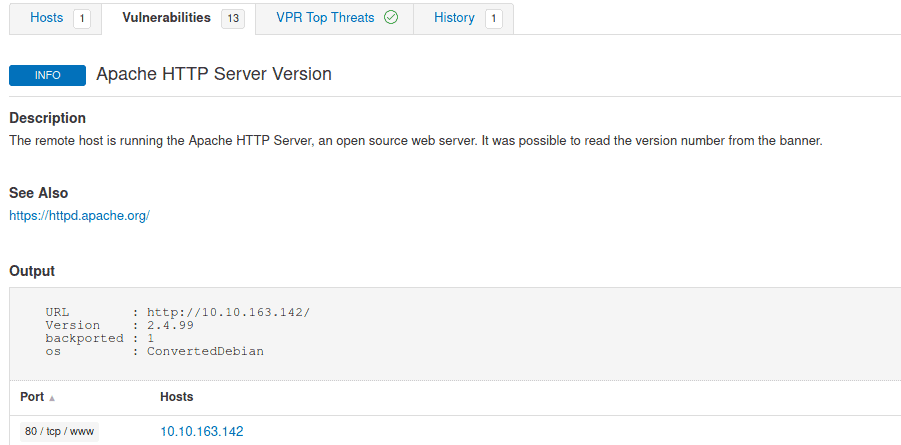
4.5 What Apache HTTP Server Version is reported by Nessus?
Open the Apache HTTP server version
You will see the version in the output
Task 5
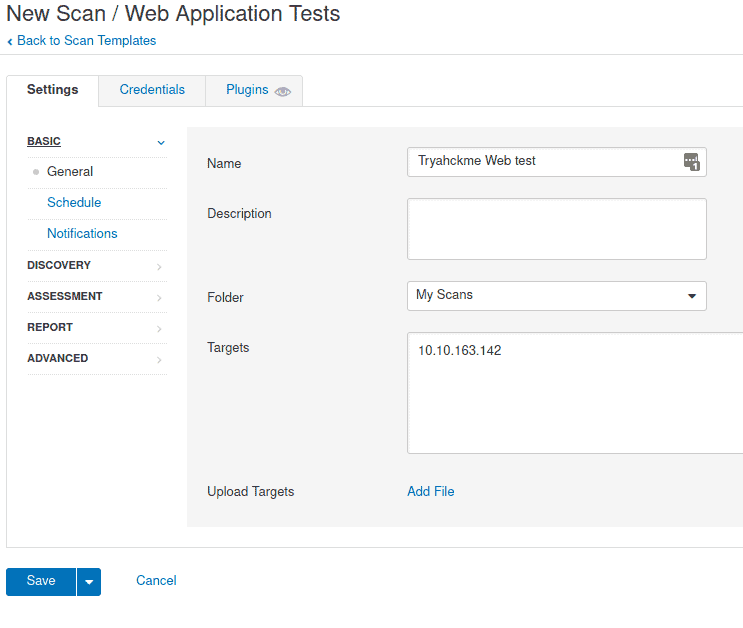
Fist we need to run a new scan
Go to My Scans and select New scan then Web application tests
Now Launch the scan. This will take a while
5.1 What is the plugin id of the plugin that determines the HTTP server type and version?
Open the scan by going to All scans and select the scan we just have created
Click on HTTP ( Multiple Issues) from webservers family

The click on HTTP Server type and Version

Look at the right side
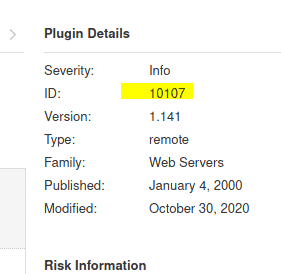
Answer 10107
5.2 What authentication page is discovered by the scanner that transmits credentials in cleartext?
Back to the Vulnerabilities of the scan. Click on Web server

Then click on Web server Transmit Cleartext Credentials
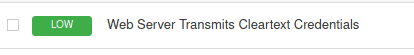
Look at the output box
Answer Login.php
5.3 What is the file extension of the config backup?
Back to the Vulnerabilities of the scan and click on Backup Files Disclosure
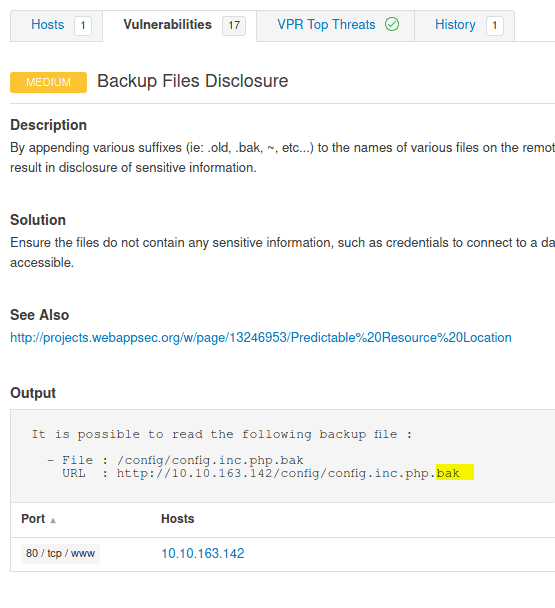
Answer: .bak
5.4 Which directory contains example documents? (This will be in a php directory)
Back to the Vulnerabilities of the scan and click on Browsable Web Directories
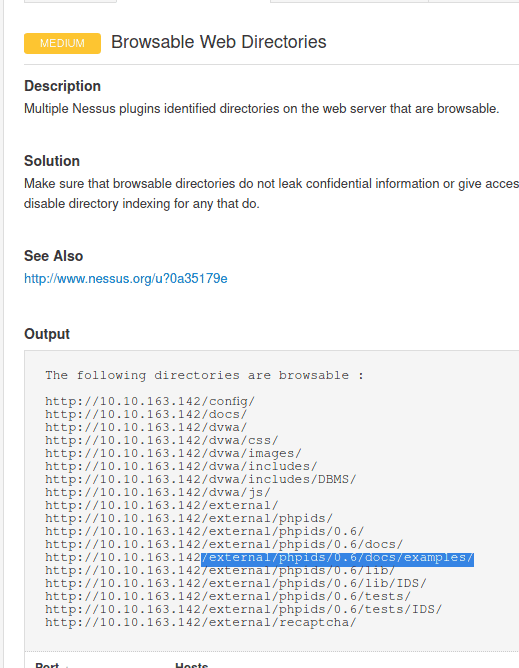
Answer: /external/phpids/0.6/docs/examples/
5.5 What vulnerability is this application susceptible to that is associated with X-Frame-Options?
Back to the Vulnerabilities of the scan and we see one other
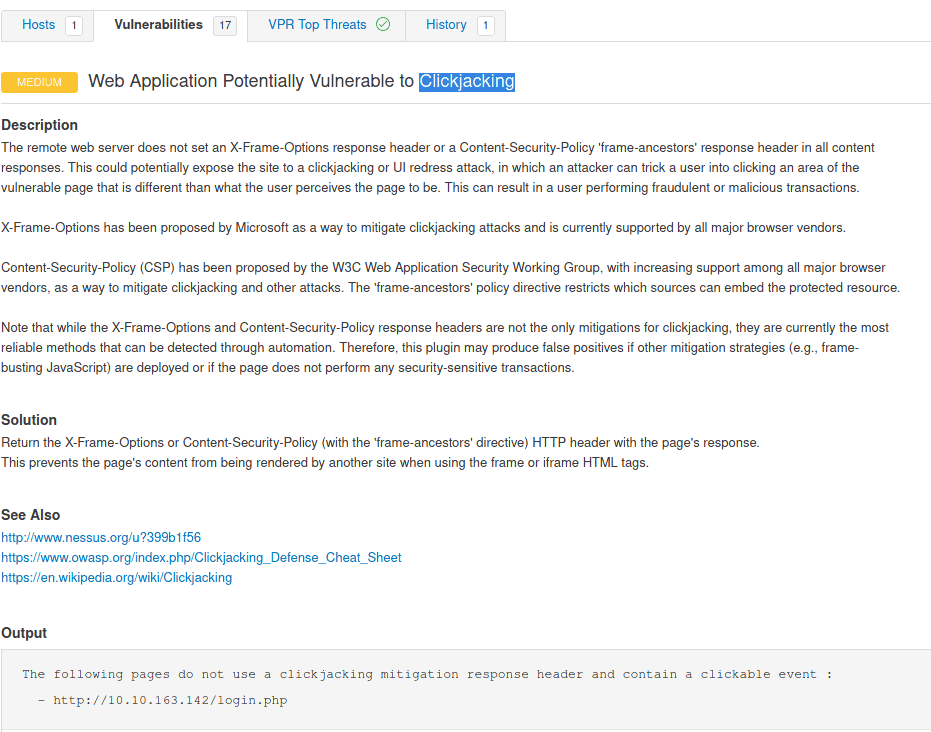
Answer Clickjacking











