This is the write up for the room Core Windows Processes on Tryhackme and it is part of the Tryhackme Cyber Defense Path
Make connection with VPN or use the attack box on Tryhackme site to connect to the Tryhackme lab environment
TASK Core Windows Processes
Task 1
Start the machine attached to this task then read all that is in this task. Use the tool Remina to connect with an RDP session to the Machine.
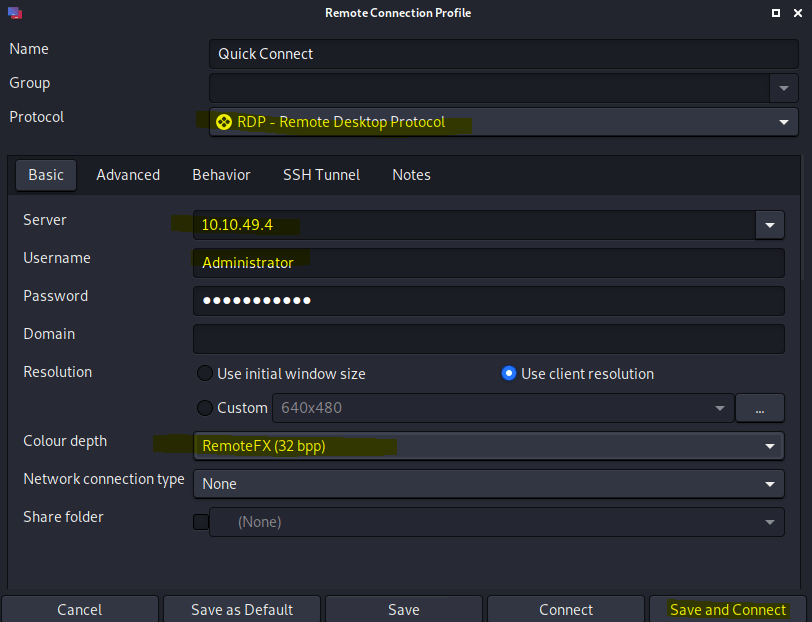
When asked to accept the certificate press yes
Task 2
Read all that is in this task and press complete
Process hacker can be found here
Process Explorer can be found here
Task 3
Read all that is in the task and do not forget to make sure you know the difference between kernel mode and user mode User mode and kernel mode – Windows drivers | Microsoft Docs
3.1 What PID should System always be?
Answer: 4
Task 4
4.1 What other two processes does smss.exe start in Session 1? (answer format: process1, process2)
Answer: csrss.exe,winlogon.exe
Task 5
5.1 What was the process which had PID 384 and PID 488?
Answer: smss.exe
Task 6
6.1 Which process you might not see running if Credential Guard is not enabled?
Answer: lsaiso.exe
Task 7
7.1 How many instances of services.exe should be running on a Windows system?
Answer: 1
Task 8
8.1 What single letter parameter should always be visible in the Command line or Binary path?
Answer: k
Task 9
9.1 What is the parent process for LSASS?
Answer: wininit.exe
Task 10
10.1 What is the non-existent parent process for winlogon.exe?
Answer: smss.exe
Task 11
11.1 What is the non-existent process for explorer.exe?
Answer: userinit.exe
Task 12
Read all that is in this task and press complete











