This guide will show you how to crack a KeePass Database file by retrieving the Master password from a Keepass database (.kdbx) file which we can use to unlock the database file to get all the passwords stored in this file. We are going to use keepass2john to get the hash that john the ripper can use to retrieve the password. I’m using Kali Linux to get the result as all tools are already pre-installed. However, you can install the tools you need on any other Linux system.
What is KeePass?
KeePass is a free open-source password manager, which helps you to manage your passwords. It stores the password in a local password database and when opening this file with the KeePass program it prompts you for the main password. Here is also the vulnerability. If you have the file we can extract the main password hash out of the file and use brute force to get this password. Once we have this password we can then use this to open the database and retrieve all the passwords
Cracking the Keepass Database file
We first need to extract the hash from the file so John can understand and crack this hash.
Open a terminal and navigate to the location of the file. Type in the following command to retrieve the hash and put it in a file called keepasshash.txt
keepass2john Database.kdbx > Keepasshash.txt
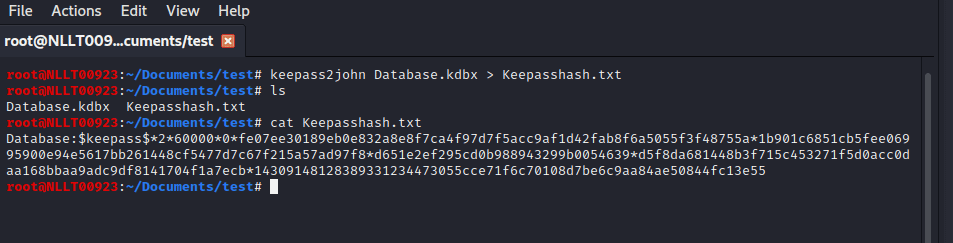
Cracking the KeePass database with John the Ripper
We are going to use a dictionary attack. This is basically a file with all command passwords we hold against the hash to see if it is correct. On Kali Linux, we already have those dictionary files. The best list can be downloaded here SecLists/Passwords at master · danielmiessler/SecLists · GitHub
Type in the following command to start John to crack the password
john --wordlist=/usr/share/wordlists/rockyou.txt Keepasshash.txt
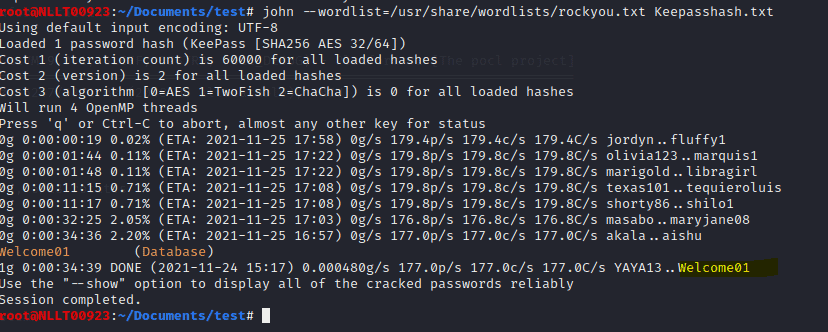
It can take a while but if the password is on the list it will crack it
Cracking Keepass database file with Hashcat and no Dictionary file
First, we need to open the hash file we have created and remove the name of the database so hashcat can handle the hash file
Type in the command
nano Keepasshash.txt
Now remove the name of the DB
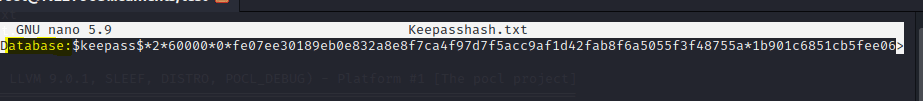
Now exit and save the file
You can also use a dictionary file with hashcat but in this example, I want to show you a way you do not need a dictionary. Bear in mind this takes a very long time to crack as it will go by all combinations
We will use the mask option in Hashcat. You can find more info here mask_attack [hashcat wiki]
Now I know and you know the password length is 9
Type in the following command to start with a mask of 1 and increment to 10
hashcat -m 13400 Keepasshashforthecat.txt -a 3 -1 ?l?d ?1?1?1?1?1?1?1?1?1?1 --increment
This takes a very long time because the password is 9 characters and I do not have this much hashing power. If you have multiple Nvidia cards you might give it a try. It is not impossible. And this is even without special characters. Read the hashcat wiki if you also want to use special characters mask_attack [hashcat wiki]
For now, I have created a second Database file to show you that it works. This file has got a 3 character password. 2 Alfabetic and one numeric.
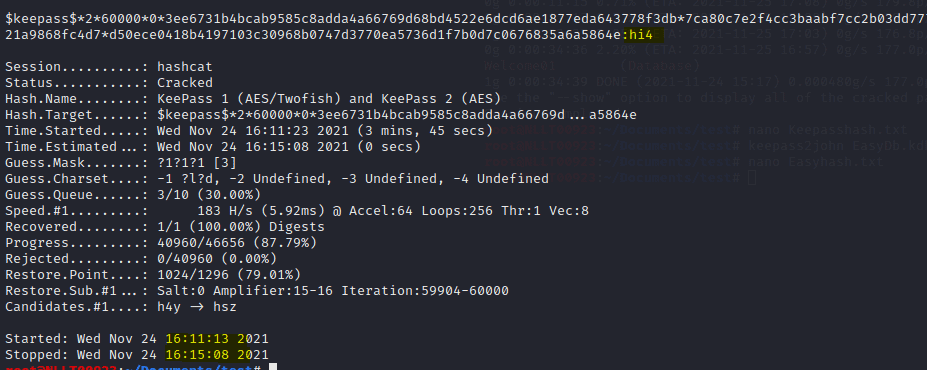
As you can see 3 characters takes about 4 minutes
Conclusion
As you can see it is very easy to crack the Keepass file once in the hand of a hacker. I store my passwords in LastPass. This is an online password manager. In this way, you can easily have a different password for every solution/website. If one gets hacked then you only have to change that password and not all. More important nobody can log in to another site you use. Never use the same password ever
If you are not comfortable storing passwords digitally then write them down. Yes, I have said it write them down. It is better than storing them on your computer or in text files. I have created a book for this you can use. Store them in this book and put the book away from your computer if you are not there. Best to save to book in a vault or other secret location. Also a nice gift for your parents or grandparents











